STRENGTHENING CYBERSECURITY: HOW ATTACK SURFACE MANAGEMENT PROTECTS YOUR BUSINESS
Software & Applications Microsoft Business Continuity FAQ Cyber Insurance May 15, 2025 9:14:58 AM Emma Elkind 2 min read
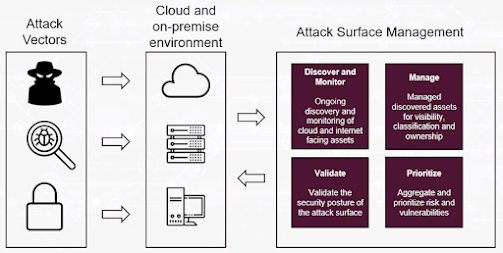
As organizations embrace cloud computing, remote work, and Internet of Things (IoT) devices, their attack surface—any potential entry point for attackers—expands significantly. Without proper monitoring, these vulnerabilities can become gateways for cybercriminals.
Attack Surface Management (ASM) provides a proactive approach to cybersecurity, allowing organizations to identify, analyze, and mitigate risks before they are exploited. This is another great tool for you cyber tool box. There are so many points of entry an ASM allows multiple sets of eyes to keep an eye on your organization.
Understanding Your Attack Surface
Before businesses can effectively protect their systems, they need to understand the key components of their attack surface:
- Applications – Any externally accessible software that could be targeted
- Websites – Company-hosted platforms that may contain vulnerabilities
- Networks – Connections between devices that cybercriminals can exploit
- Devices – Laptops, smartphones, and IoT devices linked to company infrastructure
- Cloud Infrastructure – Cloud-based services that house sensitive data
As new technologies are integrated into business operations, these attack vectors evolve, making it crucial for organizations to maintain continuous visibility and control over their expanding digital footprint.
How ASM Strengthens Business Cybersecurity
ASM helps businesses take a proactive stance against cyber threats through several key strategies:
1. Continuous Discovery of Vulnerabilities
ASM scans an organization's digital landscape for misconfigurations, exposed data, outdated software, and security gaps—providing real-time insights into potential weaknesses.
2. Risk Prioritization & Remediation
Not all vulnerabilities pose the same level of risk. ASM tools assess the likelihood and impact of each threat, helping businesses prioritize the most critical security gaps for immediate remediation.
3. Monitoring External Threats
Attackers constantly probe for weaknesses. ASM tracks threat activity and alerts businesses to potential breaches before they escalate.
4. Strengthening Incident Response
In the event of an attack, ASM helps security teams respond faster, limiting damage and preventing further exploitation.
Implementing ASM for Maximum Security
For businesses looking to improve their cybersecurity posture, adopting ASM involves several key steps:
- Conduct a Comprehensive Attack Surface Analysis – Identify all digital assets that could be exploited.
- Utilize Automated ASM Solutions – Invest in security tools that continuously monitor threats and vulnerabilities.
- Integrate ASM with Your Security Operations Center (SOC) – Ensure real-time visibility and response coordination across IT and security teams.
- Educate Employees on Security Best Practices – Train staff to recognize phishing attacks, use strong passwords, and follow cybersecurity protocols.
- Regularly Update & Patch Systems – Address vulnerabilities by keeping software and cloud applications up to date.
With cyber threats becoming more sophisticated, businesses must move beyond reactive security measures and embrace proactive protection strategies. Attack Surface Management (ASM) equips organizations with the visibility and intelligence needed to safeguard their systems, data, and infrastructure against ever-evolving threats.
By implementing ASM, businesses can reduce risks, minimize security gaps, and strengthen their cybersecurity posture—ensuring a safer digital future.
For businesses just getting started with their cyber journey or looking to improve their current system, schedule a quick call with our cybersecurity coordinator emma@attitudeit.ca or call 416-900-6047 Ext 322. Also Check out this article from Forbes about balancing budget and protection https://www.forbes.com/councils/forbestechcouncil/2025/05/14/balancing-security-and-costs-in-attack-surface-management/.
Emma Elkind
Cybersecurity Operations at Attitude IT